ETHEREUM: Private key, Public key and Addresses.
To understand the concept keys and address you have to first understand the act of Cryptography;
Table of contents

Cryptography in greek means secret writing, but in reality cryptography is far more than secret writing, secret writing is referred to as encryption which is just a subsection of cryptography, cryptography also can used to add a digital fingerprint on data for data security, authenticity and tamper proof, cryptography can also be used to prove the knowledge of a secret without revealing the actual secret, this branch of cryptography is known as Zero Knowledge Proof. Cryptography is extensively used in the Merkle tree used in the blockchain where cryptographic hash function is employed.
Now cryptography has been explained, we can dive into the main topic of the article; Keys and Addresses. In this article, you would understand what happens when you install Metamask and obtain your mnemonic phrase and ethereum addresses.
First things first, we have to understand what a wallet is. A wallet is an application used primarily as a user interface to interact with the ethereum blockchain. The wallet controls access to a user’s digital assets, managing keys and addresses, tracking the balance, creating and signing transactions. In addition, some Ethereum wallets can also interact with contracts, such as ERC20 tokens and so on. It is important to note, the wallet's primary purpose on a technical overview is to handle the keys (private and public keys) of a user. There are few types of etheruem compatible wallets, and in this article we would be focusing on Hierarchical Deterministic Wallets which metamask happens to fall under.
In this article, keys, addresses, and wallet would be simplified using the process of metamask account creation. Metamask and other Hierarchical Deterministic Wallets implement the BIP39 standards during wallet creation. First, mnemonic words are first generated. Mnemonic words are word sequences that encode a random number used as a seed to derive a deterministic wallet. The sequence of words is sufficient to recreate the seed, and from there recreate the wallet and all the derived keys. A wallet application that implements deterministic wallets with mnemonic words will show the user a sequence of 12 to 24 words when first creating a wallet. That sequence of words is the wallet backup, and can be used to recover and recreate all the keys in the same wallet or any ethereum compatible wallet application. As we explained earlier, mnemonic word lists make it easier for users to back up wallets, because they are easy to read and correctly transcribe.
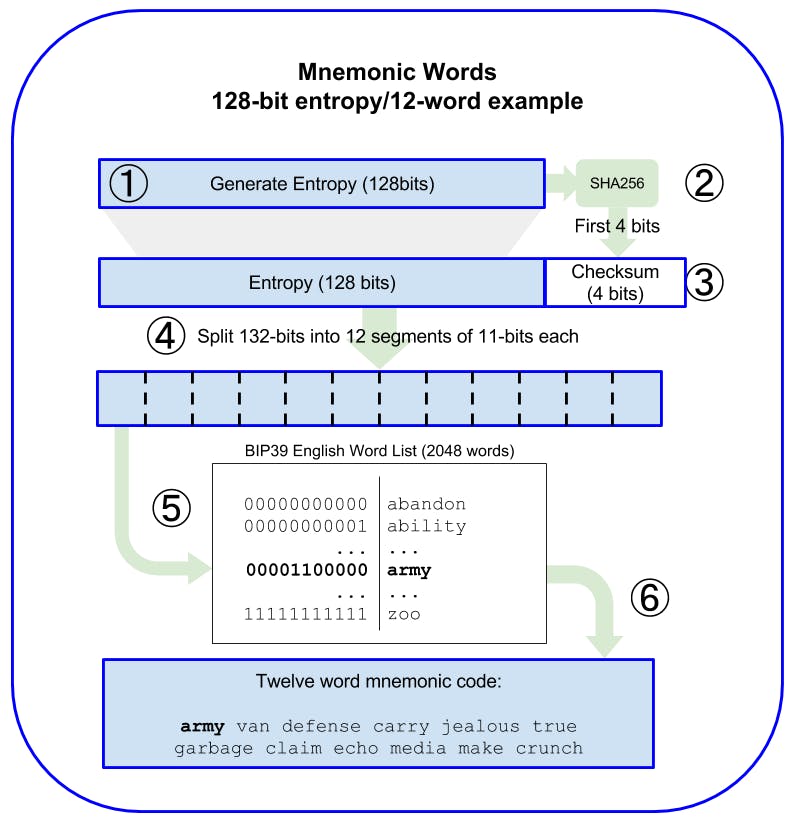
How Is the Mnemonic Code Generated ?
Mnemonic words are generated automatically by the wallet using the standardized process defined in BIP-39. The wallet starts from a source of entropy, adds a checksum, and then maps the entropy to a word list:
Create a cryptographically random sequence S of 128 to 256 bits. (Note: The higher the amount of bit used for the entropy the longer the mnemonic words generated).
Create a checksum of S by taking the first length-of-S ÷ 32 bits of the SHA-256 hash of S.
Add the checksum to the end of the random sequence S.
Divide the sequence-and-checksum concatenation into sections of 11 bits.
Map each 11-bit value to a word from the predefined dictionary of 2,048 words.
Create the mnemonic code from the sequence of words, maintaining the order.
The first parameter to the PBKDF2 key-stretching function is the mnemonic produced in step 6.
The second parameter to the PBKDF2 key-stretching function is a salt. The salt is composed of the string constant "mnemonic" concatenated with an optional user-supplied passphrase.
PBKDF2 stretches the mnemonic and salt parameters using 2,048 rounds of hashing with the HMAC-SHA512 algorithm, producing a 512-bit value as its final output. That 512-bit value is the seed.
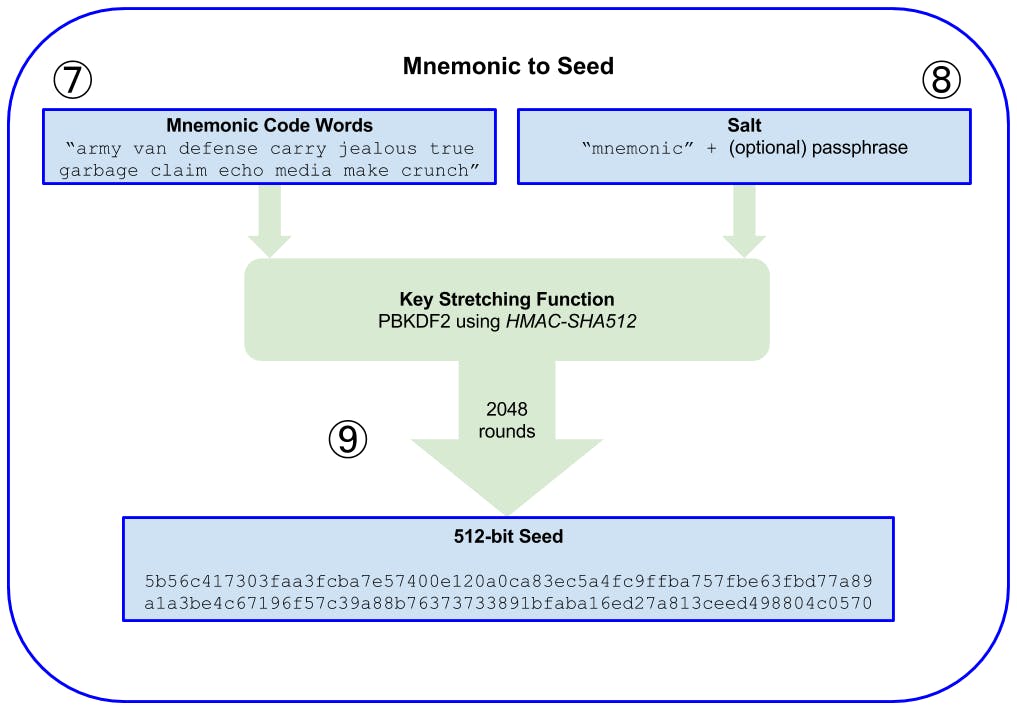
Now the mnemonic words have been generated, the mnemonic words is then used to derive a longer (512-bit) seed through the use of the key-stretching function PBKDF2. The seed produced is used to build a deterministic wallet and derive its keys. The seed should be seen as a master key because the seed is used to create an unlimited amount of accounts (private and public keys). When the private key (64 HEX character) is obtained, using the elliptical curve equation is used to generate the public key.
Now the public key and private key has been handled, we can now dive into the public address which is popularly known as wallet address where ether can actually be sent to. Public/Wallet address is obtained from the public keys. First the public key is first hashed with the hashing function keccak256 which would return a digest that is 32 bytes in length then the last 20 bytes of the digest is sliced out and prefixed with “0x” and that is the private key.
In conclusion, you have been made to understand that the security of your Digital asset lies heavily on how safe you store your mnemonic phrase because there lies the access to all your assets.